Final Thoughts
Ladies and gentlemen as a nation we as individuals can not afford to loose our nations identity and infrastructure, as humans we will require online communication it give us a essential element in our daily busy lifestyle, we really need to be self aware of future shock of the oncoming events because they at the momment are presenting a tidal wave if they come into fruition.
With over a million users now actively using the Internet in Australia for communications purposes, it is a viable ecology, yet we can not afford to let this ecology be affected by ‘Net Neutrality’, or we will be dealing with a very similar situation to what was portrayed Terminator 3 closing scene, where Jon Connor was in the communications bunker at Crystal Peak, he was standing in front of the older computer equipment, and people calling over the radio, is any body out there? is anybody reading me? we can yet afford Internet 1 to become a waste land via our ignornance towards developing nations
We can not afford to turn a blind eye to our freedoms of communication and exchanging information between each other, it is also a vital point of understanding the true freedom of information, I am worried about Australia’s Internet Future primarly because, currently we have world issues that evolve around oil supply, everything is linked to money and costs factors.
The mere fact that Oil could raise to $400.00 a barrell, how will your company survive? How will the Government of Australia react to this prospect.
To me it seems that one major aspect of this unit is that people fail to forget, that data costs money, many people forget to understand that we pay a little contribution towards the Internet as it is in our daily lives, we need it to have a affective lifestyle.
I will leave you with this question to think about, are we turning a blind-eye towards information and communication?
Thanks for your time, I would like to thank Cynthia and the rest of my Net 11 Students, it has been a pleasure to have such in depth discussions on the discussion board and thanks for all the email’s guys it has been great.
God Bless and Good Luck!!!!!!!!!!!!!!!!!!!!!!
Module Five
Module 5: Info-Communication Concepts
With considering the implications of Module Five in a reflective manner I shall try and answer each componant in a interesting manner that may include referencing material to provide a solid aspect of the questions.
- How might the metaphor of an ‘ecology’ impact on the way you think about, understand or use the Internet?
- How are the concepts ‘information’ and ‘communication’ understood within the framework of an ‘information ecology’?
- Why don’t we talk of a ‘communication ecology’?
A) How might the metaphor of an ‘ecology’ impact on the way you think about, understand or use the Internet?
Affectively establishing an understanding towards the questions requires you to develop a understanding of what the term ecology really means and what reflective aspect does it have on Internet Studies in the manner of how and what does it truely mean when being a part of the Internet and how does the ecology evolve. Ecology when looking up the term means:-
1. a. The science of the relationships between organisms and their environments. Also called bionomics.
b. The relationship between organisms and their environment.
2. The branch of sociology that is concerned with studying the relationships between human groups and their physical and social environments. Also called human ecology.
3. The study of the detrimental effects of modern civilization on the environment, with a view toward prevention or reversal through conservation. Also called human ecology.
As mentioned in Module 5, the direct interpretation of Information ecology is :-
“We define an information ecology to be a system of people, practices, values, and technologies in a particular local environment. In information ecologies, the spotlight is not on technology, but on human activities that are served by technology.”(Nardi & O’Day, 1999)
It is essential at first to understand the definition of ecology in this post to enable how ecologies change and there is a similar pattern that develops with regards to the Internet, that also develops in other ecologies. It has a definite relationship to the question of what is Internet Ecology.
The metaphor ‘ecology’ does have an impact on the way you think about or understand and use the Internet on a daily basis. As the Internet evolves it develops similary the constraints to the evolution aspect that happens in the sea which is a sad development that ecologies are meant surive and not decrease in size by sustain growth. Communication, is one aspect of developing online ecology, but communication may cause more issues and succesfully destroy’s the Internet habitat via people not fully understanding the methods and the design of the Internet. We must comprehend changes in the not to distant future, e.g. ‘net neutrality’ and aspects of it may cause fundamental flaws to develop in online ecology habitat’s, and it will be a very dangerous step in creating a man made world wide tital wave that will crash the information ecology that is now succesfully being developed by many countries.
When considering what is now online, our ecology environments such as Telstra’s Broadband is considered the BigPond, and they use this as a sales term to describe their service; within this service you have users, who on a daily basis interact on different parts of the Internet as a system to communicate. This is a very viable ecology, as the users grow and enhance their abilities on learning and adapting towards the information revolution. When considering this ISP as the big pond, the users, come and go but the environment produces enough sustainable growth in order to keep the services a float. But regulations and agreements the services flourishes daily and it allows a healthy relationship built up with a succesful customer base.
How might the word ecology, have a impact on this situation?
The enviroment is a user-based environment which has rules and guidelines that depict what the capabilities of the user can do, when looking at the Oceans laws of the sea it is very similar. We can actively say the rules for created ecologies stipulate what is allowed and what is not allowed, the environment grows as people leave and join and the growing environment and it will be guided by specific rule structure that is developed by Telstra. Humans will interact via ip adresses and communicate in many different aspects and ways that allow them to enjoy their online exprience.
How can this structure be damaged?
Viewing the ecology of the developed structure on Telstra’s BroadBand Products, you can actively see that if new regulatory guidelines constantly get established have a minimal effect on the userbase because the company still get’s users joining daily for the Internet experience. Disgruntled users have the capability of joining other broadband infrastrucutre like Optus,IINET and so on. If all Internet Service providers were effected by a dramaticly revised form regulation such as ‘Net Neutrality’ which is currently being tested in Canada, growth of product and development structure of user base would be affected and would suddenly decrease as the detrimental effects would start to take affect on the user database. Therefore the Australian Internet ecology would be affected by outside means that cause a detrimental effect on the users(organisms) of the information environment.
You can take this one step further, and compare Internet ecology to the Oceans of the World remembering that they are protected by maritime laws. Internet is a broad aspect of many different parts and functions and many nations allow their users to actively participate and actively communicate on a broad spectrum via Technological advanced means. Design flaws allow for many issues to develop in the Internet ecology, for such as pollution effects our oceans easily effects the fishing and bird life, therefore the overflow of information develops into information pollution and the effects of this are so obvious on the current aspect of Internet 1. Ecology needs to constantly grow in order to achieve sustainability, yet people will come and go on a daily basis, but the Governments of this World need to take on the regulatory requirements and remember that the Freedom of Information is the only key to success in any growing environment. Take away the freedom of information and you will be disrupting the ecology and causing a ripple effect that would be equal to an atom bomb, that will lead to a destructive measure that will damage the internet as a communication tool.
Ecology of the Australian Internet needs the organisms(humans) to flourish online and learn and develop with the communication tools that are available. Being allowed to be online is a privilege to our nation and the ecology behind this needs to be protected by the Australian Government or we will suffer greatly as a nation. We can not afford methods of Net Neutrality to become a part to our way of life or our way of thinking or as a component to the Australian Internet Ecology, we must look at these keys of success as they are vital components to the success of the Internet, like the fish in the Ocean are vital for our own life.
B) How are the concepts ‘information’ and ‘communication’ understood within the framework of an ‘information ecology’?
When understanding concept 12 you can see that that information is reliant on the communication processes in order to live and be maintained, and that there are developing humanistic and socialistic values behind the real processes of what users do on the Internet and online activities. We must view information and communication as the individual components that encapture themselves into the framework of information ecology as they are what forms the ecology, they are the parts of it that give it life. These parts are essential towards growth and development of online activivities. Each specific part has it’s own role to play online and it drives the Internet, and then creates alternative paths and routes for people to develop into and understand, Information provides a valueable source of food whilst communication can be considered the tool towards encapturing where the information is.
C) Why don’t we talk of a ‘communication ecology’?
Because ‘communication ecology’ is limited in it’s development, as it is the task of what people’s do online, communication with others. We need the information online in order to survive and understand what is happening on a daily basis, without information. There would be no purpose to online activities except congregation, therefore millions of systemless systems and nobody doing anything much except sitting their like stunned mullet. Information is the key essential part towards online growth and it gives the ability to enhance people and businesses towards new postive directions and understandings in order to enable them to succesfully grow. Information and communication need each other to surive.
Case Study: Peer to Peer
P2P refers to a ‘file sharing’ system that operates between peers.
Understanding peer to peer, the word reminds me of two computers working together like on LAN(L)ocal (A)rea (N)etwork reminds of one computer spying on the other in order to accomplish the tasks at hand, peer to peer is a very interesting topic that revolves around one word that comes to mind, is the Napster Revolution. Napster was a company that was developing a technology that would enable users to share music,video,sound,pictures online for free by sharing the information across the world. This developed into series of court cases that later developed into more people getting into serious trouble as Napster sufferred in the hands of the courts.
When contemplating the word suffered in the hands of the courts, I don’t condone the fact that Peer to Peer networks were originally established in order to breach copyright laws by providing free content that would essential take away the rights of the material from such companies as Universial Studios. Major businesses lead to the downfall of Napster. I see this whole episode as yet another flaw in Internet design where the major players never got off there hind legs and woke up to the Internet Revolution that was occurring right before there eyes. They waited for the community to get the ideas flowing and when they pounced on it to draw a quick dollar from them.
Companies are definitely at fault with regards to the downfall of the Napster Revolution and firms involved with the complaint are equally to blame as Napster was, because they decided to challenge these high rollers in court action. The firms that took on Napster should have been prepared for future shocks of Internet impact as it grew in the United States they were not prepared for the future shock that resulted in the negative output towards their company being attacked by online sources, it would have been a perfect plan to establish there own form of online peer networks at a cost, yet this gentleman went out on his own towards establishing it.
Copyright is a major concern in all peer to peer networks because people still frequently love to send files around the world, their are many different aspects of tracking and tracing these people in order to control this aspect of security breach but law enforcement can only act on known suspects, many firms do conduct online audit’s of users activities and deal with the people there and then via breach’s of AUP.
Preparing for ‘future shock”
The advanced Internet user cannot afford to become complacent in tracking these shifts – understanding the Internet is an active, dynamic and ongoing process which requires engagement with, and reflection upon, the myriad of forces and perceptions which will shape the future of the net.
Clearly understanding this as a normal user, you must be prepared for the incoming changes to what developments and advancements in technology that do occur, in order to move with the time, we have gone from Black and White Televison’s into Full Color 1080dpi Televisions, we have advanced and we have become prepared for the changes. We must understand what the requirements are, but the fact is it works two ways, we as a nation can be affected by some many different aspects of change that will interfere with the developing nation. We should be more concerned with the development of our networks, yet alone controlling the regulatory factor behind it with such mundane ideas as net neutrality.
Net Neutrality at the momment is the future shock that may await our country and many developing countries development into succesful broad band infrastructure. I use the term may await because not to much is known of the facts of ‘net neutrality’, should we be scared of this change? Simply put no, because the beneficial element of this change will cause a devastation online that would be equal to millions of users suddenly not wanting Internet any further in this country; so the future shock of ‘net neutrality’ really depends on how the Government and big business looks into the implementation of the idea, and comparing the idea towards other countries model’s.
From Module Five, some of the known ‘Future Shock’ developments include:
- Further penetration of broadboand
- Increasing delivery of multimedia – video, voice etc;
- Increasing security & authentification – smartcards, digital signatures etc
- Wifi / portable computing / communication devices
- Intelligent agents
- Semantic web
Technolgical Developments have implications on all of us, I would consider smarter ways to log in online if they were presented in a manner that was acceptable towards me. That would not include various factors of a RFID smart chip inplanted inside a human in order to make it a smarter alternative towards authentication.
Preparation is a definite key to understanding how the future develops, as you are a online information warrior, one key for surival is to always being prepared for change and developments of your online activities, but remember this line “there is no fate but what we make for ourselves”, because it really has a bearing on your online activities and online development over-time.
As I have been the ‘Net Neutrality’ talker on the forums, I will just say that my time in this land of cyberspace will finish if this function comes into reality, I will not stay or play a part in any role of the destruction or interferences of the freedom of informations and we all have our own roles to play in the protection and the future of Internet 1. No company or Government has the right to illegally profit by control measures, I personally am worried about this talk on ‘Net Neutrality’? Yes, primary reason it is a destructive mechanism to ecology of what Internet 1 is about and that is Freedom of Information.
Internet 2
“The incubator for many of the emerging technologies that are shaping the future is known as Internet2 . Formed in 1996 and administered by the University Corporation for Advanced Internet Development (UCAID), Internet2 is a partnership between universities, corporations and government agencies. … Internet2 is a not a single network, but a consortium of hundreds of high-speed networks linked by fiber optic backbones that span the United States and and link to other countries. It transmits data at speeds up to 2.4 gigabits per second–45,000 times faster than a 56 Kbps modem…”(Lerner, M)(1996-2008)
Since I have been online I have seen a lot of websites promoting different products that seem to be the answer to everyones problem, then broadband showed up on the street, I was soon connected to Optus cable and my needs were met with the cost factors being easy and accesible to all consumers. With the current construction of the consortium with regards to the NBN being built and developed in Australia to see Kevin Rudds dream of everyone having capabilities in the Digitial Economy, I still see that Internet 2 will just still be what it is today; a educational tool for the development of structured networks within the countries of China and the Americas.
Taking into consideration the technology involved and understanding the website, I have actually viewed this website many times over my years on broadband, the ideas of it are still in it’s beginner stage but the development of it may lead to succesfully developing a network capable of reaching everyones home in the future, which I guess is Kevin Rudd’s dream, but is Australia prepared for the future shock involved with this development?
When comparing the developments of the Napster Revolution and how big business was not prepared for the future shock that is existing. Is this country really prepared for the development and the ideas that are surrounded by Internet 2, with the way the current telecommunications are taking their time at constructing the NBN, I dare say it has not even been considered.
References :-
Nardi as a ecological system, Curriculum Module 5 retrieved August 27 2008, (Nardi & O’Day, 1999)
Allen M (n.d) Net 11 Curricullum Module 5. Retrieved August 27th 2008.
Lerner, M (1996-2008). Learn the Net: The future of the Internet. Retrieved August 27, 2008, from Learn the Net:Future of the Internet Web site: http://www.learnthenet.com/english/html/03future.htm
‘Net Neutrality’
http://www.google.com/help/netneutrality.html
Pollick , Michael (2003 – 2008 ). http://www.wisegeek.com/what-is-net-neutrality.htm. Retrieved August 28, 2008, from http://www.wisegeek.com/ Web site: http://www.wisegeek.com/what-is-net-neutrality.htm
Module Four
Module Four Tasks
Tools for using the Web
Bookmark Manager
Program Name :- BookMark Buddy
Cost :- US$ 29.95
Many different aspects good and bad.
A) Easy to use, very easy to understand.
B) Reasonably priced and easy to use.
C) You can use your default browser (FireFox or Opera) and manage your own bookmarks.
D) Imported all my bookmarks easily.
E) Keyboard shortcuts are a bit awkward.
G) Customer support is lacking
Offline Browser/Copier
Program Name :- Webcopier
http://www.maximumsoft.com/products/wc_windows/overview.html
Cost :- $30.00, $40 life time subscriptions
A) It is a powerful tool that stores them locally, on your system, until you are ready to view them.
B) Specially-designed Wizards will help you create each new download project.
C) $10 extra for life time subscription, makes the program worth it.
Searching the Web
What to do:
1. Choose your most commonly used internet search engine and do a search with words of your choosing.
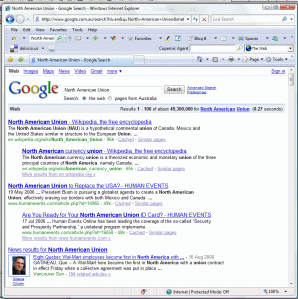
I decided to use www.google.com.au and search for the words North American Union.
Noticeably there was over 49, 300 results with the search engine.
2. Using copernicus or similar, set it up to search at least three search engines (including one that will search the ‘deep web’) and repeat eactly the same search
LOG ENTRY: record the number of hits in your learning log, and compare to your first search. What differences did you notice? Why? Which search, on first glance gave you the most promising results?
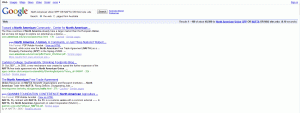
Using Copernic’s Basic Agent I recorded 5 hits with, it was a unique program that actually shows the relevancy of the search by percentage value.
Getting a little curious I was dumb-founded by the term “Deep Web Search”, does this mean I am searching further than the titanic? Going down into the deep and dark places of the Internet? Well am not 100% sure of what and why they would be saying “deep web search” but after reviewing the documentation in the web tasks it became a clearer and I understood more on what to do.
Went back and used the copernic’s search engine that was available by looking at the right hand side of their site right at the top, the number of results that came back was similar to the google search.
Boolean searching task
Taking the same key words of your last search, think about how you would best search for the following:
- the biggest number of hits relating to these key words
- information most relevant to what you ACTUALLY wanted to look for!
- information coming only from university sources
LOG ENTRY:
Discuss your strategies with the class and record the exact search terms you used in your learning log
Firstly I decided to test www.dogpile.com to see what happens and the results, there is a method that allows you to use the extended preferences but not as detailed as www.google.com.au.
Dogpile never impressed me at all, it was too bland and too basic type of search engine, I am a google fan, it works it gives you what you need.
I found dogpile a less form of google. Too me a search engine that works on it’s own is a primary source of interest so I switched over to google advance to achieve some vastly better results.
Organising search information task
First, choose the best three sources found in the previous task (and be aware all these sources and information can be contributing to your resource bank assignment!)
I would like to stick to the issue that I previously discussed with regards to the North America Union as it is a topic that will flare up in the not to distant future, so in order to understand the future we must first stop and read and comprehend what is going on.
URL:- http://www.american.edu/ia/cnas/pastortnac.html
Author :- Robert A. Pastor, C. Fred Bergsten (Preface)
Institution :- American University Center for North American Studies
This book describes Robert Pastor’s ideas with regards to the modernisation of the United States, Canada, and Mexico into one enity, with the possible aspect of having a larger market capability than that of the European Union. Robert Pastor’s book, describes proposals for constructing a North American Community. It is a visonary study, Robert Pastor’s maps out the paths towards making a North American Union a reality.
URL:- http://www.american.edu/ia/cnas/pdfs/Pastor_Worldnet.pdf
Author :- Robert A. Pastor
Institution:- American University Center for North American Studies
This document seems to have been created by Robert A. Pastor to defend his ideas. By describing current reactions by many high ranking profile reporters, writers, critics that have and are continuing to study into Robert A Pastors dream of creating a North American Union. Robert A. Pastor defends his ideas and interpretations of the North American Union and the effects it would really have on the United States, Canada, Mexico. Claiming that the critics are spreading false information with regards to the creation of the North American Union, defends himself by establishing a arguement about the truth’s behind his book. He then defends his ideas and basically establishes his argument of what his book is about. Why are his critics so against it by demonstrating the ideas and how wrong his critics are with regards to his ideas. In closing he re-aligns the fact that it would be far better for each three states to have a better relationships established than what is currently happening and the fear mongers are wrong, because all is what is needed is the breaking down of the barrier’s in order to create a better relationship.
URL:- http://apps.carleton.edu/campus/sustainability/Shrinkingfootprints/?story_id=346841
Author:- Katie Blanchard

- NAFTA

For evaluating the web, I decided to stick to the American University for North American Studies article because it was a defensive post with regards to Rober A. Pastor’s book that he created based around a obessive arguement that United Stated of America, Mexico and Canada should be combined as one to form the North American Union. In this article he is defending his idea and also identifying the perpertraitors and debates and why they can not affectively associate themselves with the truth behind the greatest concept every devised.
URL:- http://www.american.edu/ia/cnas/pdfs/Pastor_Worldnet.pdf
Author :- Robert A. Pastor
Institution:- American University Center for North American Studies
This document has been created by Robert A. Pastor to defend his ideas, by describing current reactions by many high ranking profile reporters, writers, critics that have and are continuing to study into Robert A Pastors dream of creating a North American Union. Robert A. Pastor defends his ideas and interpretations of the North American Union and the effects it would really have on the United States, Canada, Mexico. Claiming that the critics are spreading false information with regards to the creation of the North American Union, he defends himself by establishing a argument about the truth’s behind his book. He defends his ideas and basically establishes his argument of what his book is about. Why are his critics so against it by demonstrating the ideas and how wrong his critics are with regards to his ideas. In closing he re-aligns the fact that it would be far better for each three states to have a better relationships established than what is currently happening and the fear mongers are wrong because all is what is needed is the breaking down of the barrier’s in order to create a better relationship.
The article was written by Robert A Pastor a member of the Council of Foreign Relations. He is a very dedicated and unique person who has a credibile background in Politics. He earned his Bachelor’s degree in History from Lafayette College and a Masters of Public Administration and Policy (MPA), with a concentration in International Economics from the John F. Kennedy School of Government at Harvard University. He also holds a PhD from Harvard in the field of political science. He served in the US Peace Corps in Malaysia where he learned the Malay/Indonesian language. He also was a Fulbright Professor at El Colegio de Mexico in Mexico where he taught courses on U.S. Foreign Policy.
The article contains document that there is alot of evidence being presented that is false allegations being created by high profile media reporters with regards to the creation of the North American Union, he defends himself by stating that these allegations are false and misleading towards what he is expressing within his book. If these people clearly understood what the book was created for, they would understand the necessity towards the creation of the North American Union. He then suggests that people become aware to the true facts by visiting the website www.american.edu/ia/cnas.
Then presenting the article in a manner that suggests to me he is defending his book in five points that are summarized so that you can affectively understand why there has been misinterpretation about his book. He establishes five facts on why is it necessary for the creation and establishment of a North American Community and the basis of this community.
When considering future use of the review, the annotated review of the site would become much handier to have as it is a understanding of the document and what it is about. Breaks down the necessary points of what is contained in the full article without having to read the full article, very handy if you don’t have much time on your hands and require document access sharply.
References :-
Robert, Pastor Toward A North American Community. Retrieved August 27, 2008, from http://www.american.edu/ia/cnas/pastortnac.html Web site: http://www.american.edu
Pastor, Robert Toward A North American Community. Retrieved August 28, 2008, from http://www.american.edu Web site: http://www.american.edu/ia/cnas/pdfs/Pastor_Worldnet.pdf
Blanchard, Kate (October 31, 2007 ). Revisiting NAFTA. Retrieved August 28, 2008, from http://apps.carleton.edu/campus/sustainability/Shrinkingfootprints/ Web site: http://apps.carleton.edu/campus/sustainability/Shrinkingfootprints/?story_id=346841
Conceptual Research and Reflection Project
Concept 7: Netiquette
“Netiquette”
“Good communication practice on the Internet is not something one ‘learns’, but something one practices’ so as to teach others, less familiar than yourself, how it is done.” (Allen, n.d)
People join the Internet daily without realization of what the Internet offers and the advantages of asynchronous electronic communication that still requires them as a citizen to participate in a friendly and out going manner not holding back their thoughts but develop them in a friendly and social manner.
We have to remember that within the Internet Info sphere we co-exist with other humans, what ever experience you gain don’t ever let it cloud your memory towards helping others. Netiquette describes ‘good’ and ‘bad’ conduct in online communication (amongst other forms of Internet use). But what is important about Netiquette is the concept that there are these ‘agreed’ rules of what is good and bad.
Reflecting over the work that has been achieved over the previous months and developing the skills of communicating with my fellow net citizens to me one correct principal sticks out with each and every student that has come to me asking for advice, “treat others how you wish to be treated”. This quote has so much impact, the fact is that this is what one of the core aspects of netiquette.
While it’s good to focus on the aspects of being responsible net citizens and the friendly and most kind way they react to people, it’s often the people who have not much experience with online activities that often fail to address people in the correct manner that leaves their presence online in a negative manner. People who often sit behind a computer fail to forge the human element which then creates there attitude into a invincibility cloak becoming a part of them that deceives not only themselves to the correct methods of the way to and react to situations that develop online but often will contribute to their Internet activities demise.
“The golden rule your parents and your kindergarten teacher taught you was pretty simple: Do unto others as you’d have others do unto you. Imagine how you’d feel if you were in the other person’s shoes. Stand up for yourself, but try not to hurt people’s feelings.” Shea, V (2006)
While logged in on the internet we must now understand and develop ourselves along the basic main facts that are now presented in this document, that when humans are interacting on the internet we all become key elements in the attention economy, where you will be constantly attacked and bear some brunt of full forced verbal abuse and attacks.
Developing your knowledge while on the Internet is your best option; it brings people like yourself aware of the key parts of internet communications like net etiquette. Rules were established in October 1995 via the creation of the rfc.1855 Netiquette Guidelines. These guidelines are an established set of rules that allow you to understand what the acceptable form of net etiquette is.
Internet Communications requires greater thought when speaking online and you and always remember that the Internet is not only created for the freedom of speech but to be able to talk and teach others from correct and proper use of it. Following the established rules will give you greater mobility but capability of establishing new friendships and developing them via understanding the correct terminologies of netetiquette.
Site 1:
Shea, Virgina (1994). Netiquette. San Francisco CA 94118 : Albion.com. Retrieved July 30, 2008; http://www.albion.com/netiquette/rule1.html
Evaluation
Interesting book that has applied the facts from previous articles into a more comprehendible book that applies additional facts about the topic by suggesting to you the best way to understand what are the requirements of the Internet and how you are to respond towards issues that arise. Going into the descriptions provided in this book it allows you to understand what and how it is vital to understand the inner workings of the Internet before you enter into the brave world of cyberspace, this book explores all facet’s and gives great details on how to respond and act in the public arena.
Site 2
Hambridge, S (1995). Netiquette Guidelines. Santa Clara, CA 95052: Intel Corp.. Retrieved July , 29 July 2008; http://www.rfc.net/rfc1855.html
Evaluation
These guidelines form the basic structure of what is responsible and what is negative output towards a developed rule structure for online activities. Created after the previous book was written, it interprets a lot of the actions for online activities of users and what is the proper way to respond and develop oneself towards correct Internet responsibility. Development of responsibility is one of the core aspects of this paper, it can lead to greater success in online activities and creating the happier established environment. Bearing in mind the different types of activities emails, Internet Relay Chat, that are online activities it gives you greater established ideas on how to respond to people in the positive manner instead of irresponsible ways that lead to arguments being created.
Concept 26. Privacy and Security
Privacy and Security
“The Internet is a profoundly ‘open’ system and advanced Internet users are cautious about either accepting or sending material from and to unknown sources and are careful in releasing information about themselves in any form. Conceptually, the Internet challenges us to take greater responsibility for the protection of privacy and security than perhaps we are used to when dealing with the media.” (Allen, n.d)
People join the net daily without the realization that they have exactly the same societal responsibilities as that of when they go to the supermarket. They have to remember that it’s not only a social responsibility to control their social habits online, but have to ensure that they protect there security and also privacy as the Internet is a open system.
When conducting themselves online they must protect their own identity, Internet Communications is a broad spectrum of emails and various chat programs, and various types of Internet browsers that could be manipulated to gain your data, therefore you need to be sending secure data over the Internet by using various Ad ware programs and Virus Software’s and most of all ensuring that your encryption in your Internet Browser does not fail or is interfered with.
And these need to be kept up to date on a constant basis to protect the user from any malicious software from destroying there information, as there are many forms of information that you are being involved with online, your activities are monitored by not only you but other sources do have the capabilities in tracking your information down, learning is the key essential to understanding how you are online.
Like driving a car you need to gain experience online and it is vitally important that you know how to use your web browser. “You may be “shedding” personal details, including e-mail addresses and other contact information, without even knowing it unless you properly configure your Web browser” McCandlish, Stanton (April, 2002).
Establishing online education is a key component, police have now developed over the previous years, as the net has evolved so has the policing abilities to ensure a greater community awareness occurs, in order to decrease the online issues with various privacy scams.
Personal privacy is one key online element that you need to respect, but also protect from the undesirable criminals, you need to develop your understanding in this area, or this will leave you open to various types of attacks via email, and other types of computer software by criminal elements who will try and achieve to disrupt your access and interfere with your financial information that wish to ensure they get a hand on your privacy information and personal financial information. It is vitally important not to allow the criminal’s access to you by developing and understanding of what you are doing and in this not allowing access to your information by using control measures.
“Knowledgeable individuals can take steps to prevent their web-surfing practices from being captured by the web sites they visit. But, realistically, few people have the requisite knowledge or patience to take advantage of such privacy-enhancing strategies via using encryption measures.” Givens, Beth (2001,March).
You can include all the security in the world on your computer but it really comes down to the fact of being smart and knowledgeable in order to stay above the problems, for example Internet users need to be wise and watch for the information that the government websites are trying to teach them because that is where the core aspects of the Internet evolve from. This is the only way that they will be successfully getting serious knowledge on how to handle themselves online without the hassles of privacy and security breaches.
Site 1
McCandlish, Stanton (April, 2002). EFF’s Top 12 Ways to Protect Your Online Privacy. Retrieved July 30, 2008, from EFF’s Top 12 Ways to Protect Your Online Privacy Web site: http://www.eff.org/wp/effs-top-12-ways-protect-your-online-privacy
Evaluation
Electronic Frontier Foundation is a highly developed contextual information website that not only assists the Internet community with developing issues it also takes them on in the court room, it is the last frontier for Internet consumers who wish take raise complaints about the rise and fall of freedom of speech online. Dedicated to privacy and also security of the individual and given key examples of this in web links and also a lot of documentation provided and they keep a watch on companies who fall from the top to ensure that the consumer is being looked after, they are a vital component of the internet community because they assist and believe in the creation of a happy and safe internet environment.
Site 2
Givens, Beth (2001, March). http://www.privacyrights.org/ar/Privacy-IssuesList.htm. Retrieved July 30, 2008, from Privacy Today: A Review of Current Issues Web site: http://www.privacyrights.org/ar/Privacy-IssuesList.htm
Evaluation
Privacy Rights is dedicated to the similar issues as Electronic Frontier Foundation, it has contextual information on the website that allows you to get a clear and defined answer to many different issues that occur in privacy and security. Privacy rights are a non-profit organization developed to assist you in understanding what your legal rights are via online education with clearly defined information. Clearly defined goals has allowed Privacy rights to raise consumers awareness of how technology affects personal privacy, and also has shown people on the Internet how to empower themselves as consumers and to take action to control their own personal information by providing practical tips on privacy protection.
Concept 17. The impact of text-based real-time chat
The Impact of text-base real-time chat
Communicating in real-time with text enables a form of ‘authoring of the self’ that is similar to the processes of face-to-face speech but which is much more amenable to authorial control, experimentation and reflection. Further, text-based communication carries with it the possibility for multiple, differing conversations occurring simultaneously, relying on the ability of the human brain to deal with text much better than speech.
As the evolution of the internet continues and broadband expands over time, we have seen so many different aspects of virtual communications develop successfully and over time it has allowed the emergence of various sustainable virtual communities. These virtual communities are the global hub of the internet, communicating is the most important aspect of this community and developing the communication towards others is what many do on a daily basis via email, chat programs, and messengers.
“Most notable development happened in 1989 when Internet relay chat was created. It was originally implemented for users on a Bulletin Board Service to chat amongst themselves (rfc2810)”.
It was soon noted after the development of this tool, issues arise and questions remained on how to control the people within the virtual world of the program, admin tools were developed into the program and netetiquette soon became a stronger tool to support this programs life, in that it maintained the law and order.
“IRC, like most internet services, is usually accessed through a client program, which connects to one of a number of interconnected servers, which then relay the messages around the world. When connecting to a server, the user chooses to listen to one or more channels, which usually have a theme or subject. The chat happens in real time, though sometimes there is a delay in the relay, called lag, which is caused by sections of the Internet being congested, or one of the serves being overloaded.”(Stringer, Gary (1999-2005 )
Many aspects of communication on internet services have a great deal of anonymity with them and relay chat has not developed a secured method of developing past this. Relay Chat allows a user to control the who and the what he wants to be, giving them the chance to join and rejoin servers as many different identities, if he feels the need to be, therefore it is a semi-insecure protocol that is only bound by what Netiquette rules that are applied to the servers structure.
Developments have always continued with text-based real-time chat and many different types of programs have been developed off the success of Internet Relay Chat, which saw the emergence of text based games as dungeons, and the development of Muds and Moo types of online character based game play. These games developed a virtual world for the user to explore, which allowed the user to use their creative mind and control the inner workings of there developed game.
Progression has seen the successful development of text based real-time chat and also voice based real time chat, that has not only allowed extended benefits to the gaming communities but has allowed the programmers to bring the community closer together as they play there video games in a truly new aspect of a virtual 3D world, so the progression past the start has certainly taken many turns for the better as the technological aspects have been applied to many types of software.
Hence as the ideas progress, the same issue has still remained how to control voice time chat as the security behind it requires users to run there own software in case they become a victim of a angry person or a perpetrator.
Unlike text based chat voice based chat is harder to identify issues as it is a requirement of the user to have software running in the background in order to capture video files of users being disrespectful towards others, any evidence is quickly dealt with better than hearsay evidence, so as we progress we still hit the major issue of security problems when it comes to evolution of text-based chat products.
Site 1
KALT, C (April 2000). Internet Relay Chat: Architecture. Retrieved August 1, 2008, from Information Sciences Institute Web site: http://www.isi.edu/in-notes/rfc2810.txt
Evaluation
This text deals with the evolution of internet relay chat and how it developed and evolved over time to what it has become today in our virtual world. Text branches out from how it was early designed for usage on Bulletin Board Services and then established itself on what we now know as the internet. Text based conferencing is a about the clients that are involved and how it works via servers, basically describing the full architecture of how it operates and how the controls work on the network in order to keep it running correctly.
Site 2
Stringer, Gary (1999-2005 ). Virtual Communities. Retrieved August 3, 2008, from Creative Media Information Technology Web site: http://www.services.ex.ac.uk/cmit/modules/the_internet/webct/ch-communities.html#id799913
Evaluation
This lecture looks at the applications that allow synchronous, real-time interaction and communication. These vary from simple systems to send real-time messages, to virtual worlds where you’re free to wander around in a world that only exists in the computer’s memory. Lecture also provides various answers to what text communication is all about and how it has progressed over time and then moves onto what virtual reality is about and how netiquette provides the necessary societal requirements in order to keep order on the net communities that have formed.
Concept 33. Information and attention
Information and attention
In the era of the ‘attention economy’, readers and users of Internet information must be carefully craft, in their own minds, the kind of metadata which will – almost instinctively – ‘fit’ with the metadata of the information sources they want, so that – in the few brief moments of initial exchange, when a seeker of information encounters information being sought, rapid, effective judgments are made that ‘pay off’ in terms of further reading, accessing and saving.
Looking over history and the developments of public speaking, the most notable public speakers may it be Stalin, Roosevelt, Hitler, and Menzie’s, each had their own method of gaining public attention via the correct method of handling the information. Observing the previous public speakers, you see the theory of public speaking in working fact, most important fact is that every seven minutes you must provide information that keeps the audience enthusiastic, otherwise they will go to sleep, the similar familiar approach is taken with World Wide Web development you need to provide information that keeps your audience enthusiastic.
Handling information requests and addressing information correctly is an important function that needs to be looked at, so World Wide Web development can be addressing the public search engines in a correct manner. Emergence of the new buzz word known as the “attention economy” has allowed the most vital and true component of web development finally come forward. “Attention Economy” sees a broad range view of many different aspects of net culture, but one aspect it looks at is how to effectively establish valuable web page content, which encourages the user to maintain their website. The constantly evolving Internet has seen web page creators have to get smarter in programming and development and design by getting expertly creative in their ideas, in turn this development has seen vastly better and fresher web page content derived.
Looking at information we discover two sites that remain a constant feed of information for users are Facebook and Myspace, they not only feed information but also grab the attention of the public. The sites allow users to have complete control over their web page design; it allows them to be the creator of their attention. It also allows them to control what they do on the page, therefore has become the necessary new requirement of someone Online’s activities.
“The basic ideas behind the Attention Economy are simple. Such an economy facilitates a marketplace where consumers agree to receives services in exchange for their attention. The ultimate purpose is of course to sell something to the consumer, but the selling does not need to be direct and does not need to be instant”. (Iskold , Alex (March 1, 2007 ).
Interpretation of what is required in content, and understanding the requirements of the users of the attention economy is the two key crucial elements, but by viewing the millions of the poorly designed web pages you begin to understand and familiarize yourself with the key picture of requirements.
The main key elements of the attention economy for the world wide web are quite simple, “people rarely read Web pages word by word; instead, they scan the page, picking out individual words and sentences.”( Nielsen, Jakob (1997).)
Poorly designed web pages sit dormant and abundant in cyberspace because people failed to address the key requirements of web page creation. They wanted a webpage because their friend had one, similar to the current group aspects of my space and face book, which would have enabled them to get behind the crowd and encourage the crowd to listen to their points of view and understanding.
“The idea behind the Attention Economy is to create a marketplace where consumers are happy, because if they are shown relevant information – then retailers are happy too, because happy consumers spend money!” (Iskold , Alex (March 1, 2007 ).
Many of the public speakers mentioned earlier, over time remained at the high point of their political life as the person in charge and person in the know, because they knew the key requirements on what they believed and wanted in the world, they knew how to address the attention of the people that grew into economy of people over time. Relevancy is the key requirement of information and attention it then allows you access to millions of hits that will enable your site to gain the attention needed to survive online as you would have successfully dealt with the issue of irrelevant content.
Site 1
Iskold , Alex (March 1, 2007 ). The Attention Economy: An Overview. Retrieved August 4, 2008, from The Attention Economy: An Overview Web site: http://www.readwriteweb.com/archives/attention_economy_overview.php
Evaluation
This site provides in great detail what is expected from providers of information, by providing the necessary requirements by addressing the key points with regards to the attention economy. It breaks down the common goals of what the attention economy is and then derives in the sub headings how to affectively overcome the common issues and then employ ideas on what happens and why it happens and then focuses on the final outcome of what are the challenges ahead.
As this topic is a great interest of mine I felt I had a great interest to the topic at hand because many parts of the information provided were so detailed it opened up the key points on what happens online with information and attention and so I learned a great deal from this.
Site 2
Nielsen, Jakob (1997). How Users Read on the Web. Retrieved August 6, 2008, from How Users Read on the Web Web site: http://www.useit.com/alertbox/9710a.html
Evaluation
Creating a webpage this site would be the key ingredient in the information selection for it, the site goes into great details on what is the best way to present information in web development. Nielsen’s paper was the building block to current webpage design, this was written in 1997 but in todays webpages you can still use the same core aspects of this paper. It not only developed the same ideals, it has encouraged development towards redefining what is good about the Internet and what is bad. Nielson’s paper not only encouraged the early net but allowed people to pick up on his ideas and use them to push the World Wide Web along in development.
Bibliography
Shea, Virgina (1994). Netiquette. San Francisco CA 94118 : Albion.com. Retrieved July 29, 2008; http://www.albion.com/netiquette/rule1.html
Hambridge, S (1995). Netiquette Guidelines. Santa Clara, CA 95052: Intel Corp.; Retrieved July 29, 2008; http://www.rfc.net/rfc1855.html
McCandlish, Stanton (April, 2002). EFF’s Top 12 Ways to Protect Your Online Privacy. Retrieved July 30, 2008, from EFF’s Top 12 Ways to Protect Your Online Privacy Web site: http://www.eff.org/wp/effs-top-12-ways-protect-your-online-privacy
Givens, Beth (2001, March). http://www.privacyrights.org/ar/Privacy-IssuesList.htm. Retrieved July 30, 2008, from Privacy Today: A Review of Current Issues Web site: http://www.privacyrights.org/ar/Privacy-IssuesList.htm
KALT, C (April 2000). Internet Relay Chat: Architecture. Retrieved August 1, 2008, from Information Sciences Institute Web site: http://www.isi.edu/in-notes/rfc2810.txt
Stringer, Gary (1999-2005 ). Virtual Communities. Retrieved August 3, 2008, from Creative Media Information Technology Web site: http://www.services.ex.ac.uk/cmit/modules/the_internet/webct/ch-communities.html#id799913
Module Three
HTML
Record your thoughts about html – do you feel a sense of achievement?
Over the last week I enjoyed learning about the advantages of html, and learning how there were many important commands that allowed you to develop your page. Like morse code, looking at what you write in html is highly important because if you do not type in the right code to the page you will succesfully mess your page up.
Using all the commands and going through and completing the whole 26 lessons first, then I went back and picked the easiest ones to remember and put them on webct ipresentations part of the Curtin website. I don’t feel a sense of achievement because my coding is rather not 100% tidy, entering the codes into the script and waited to see the outcome, if it worked it worked if it didn’t I would start again.
Do I think I have learned something? Yes, but I do think I can learn more and develop what I already have started to progress in. I do not understand CSS and I will be honest with you, I think it’s most likely easy to understand.
What are the differences between html and blogging?
Html is a form of coding that requires you not to only input the correct code but also validate that code correctly whilst creating the webpage via progress. Blogging is a direct dynamic way to enter code and create a page on the web, I prefer blogging over html because it’s easy and requires very little to maintain it.
From what I learnt about validating the code, I really made a serious mess of my html page, but I guess that is cool because it’s the only page that I have ever created, I pray that the lovely Cynthia forgives me for my lack of knowledge on this.
Optional ‘standards’ task:
Make a summary of what you believe are the 5 most important ‘rules’ for writing online. Think about any differences between the articles: for example, is the advice in Nielsen’s paper — written in 1997 – still current?
My Summary of 5 most important rules for writing online.
1. When establishing your web page please use concise and clear language.
Clear language is the most essential part of good web writing, developing your skills here is essential because you have a more wider audience than just one person viewing what you write. People want clear and concise language, and language they can assimilate and take in without any hassles of interpretation.
2. Users want there information quickly
When I visit webpages, I hope that many of the links of the valueable information that I am seeking work, what a great dissapointment when studying into geneology is the fact of some links on certain sites just go 404 File Not found, yes people do move on but there needs to be a update added by the current site to maintain the sites credibility.
Organisation is a key aspect of the site, I want a clear cut picture on what they offer for information as I seek it not be moved around from site to site searching, if people are capable of providing the truth it should be able to be said in one clearly defined website.
3. Do all your links actually work?
Links are as vital to the website as they provide clear background evidence towards what the site is about, what the sites ideas are and where if any further information can be found to enhance the sites current information.
But not only those types of links are essential, but graphic links, I have visited some people’s personal webpages and yet you still come across the vast few people who do not fix up imageshack.us photo’s that have been taken down off image shack and they let the site dry up.
Their is a gradual annoyance towards sites that links don’t work, it really comes into a category of unprofessional web site design and building. Maybe their should be some sort of code that allows admins to delete webpages, users have a alert that their webpage needs to be fixed within 30days or the website will be closed. This in turn would save people time, and also saved the load of amateur behavior of not fishing websites or keeping them updated with current and vital information.
Links really should be treated as valueable as the information that is contained on the website itself.
4. Are your pictures small enough?
Within the older days of dialup this was a significant issue as the pages of your website would take time to develop similar to a photo copier. Todays current enforcement of download limits it is yet again a vital component towards a succesful fast web page requires the element of succesfully placed photographs and graphics, that allow the page to flow freely.
Noticing on many sites that I have viewed that people get to side tracked on how great they can make their webpage yet have very little viewers because they forget the basics of webpage design. Very important to read about website design before creating and co-relate that information into your site and graphics is the key element to add the visual effect towards keeping hits happening to a decline in visits.
5. Is your content significant?
Having the website content significant is a great deal towards keeping the happy person entertained with the goal of what the website is about and the value of information that is contained on it. Depending on what website you have created and what purpose that website proposes.
Content is a highly significant aspect of website design, you need to constantly change and update your content depending on why the website was created originally, it’s like many sites take constant hits because of the value of the information on that site.
For example , Alex Jones Site Infowars.com, vast majority of content on this site is constantly changing as they find more information to spread the word across to their listeners. Content is many different subjects that are happening in the gray field of US Politics, but yet again it deals with one main core aim Of US Politics. They need valid content to be constantly getting hits, but on the other hand needs to push truth of information in order to keep valid listeners to the radio show that uses the website to push there web agenda.
Impact of Nielsen’s paper — written in 1997.
Nielsen’s paper was the building block to current webpage design, this was written in 1997 but in todays webpages you can still use the same core aspects of this paper. It not only developed the same ideals, it has encouraged development towards redefining what is good about the Internet and what is bad.
This paper can be defined as the building block for a variety of reasons that are current with such webpages as top 5 conventions of web pages by Dennis G. Jerz as alot of Nielson’s paper are contained on this current website.
Nielson’s paper not only encouraged the early net but allowed people to pick up on his ideas and use them to push the World Wide Web along in development.
LOG ENTRY:
Record the url of your uploaded page in your weblog
After validating my webpage I uploaded it to the ipresentations area.
http://webct.curtin.edu.au/305033_b/student_pres/Group05/index.html
Blogs
In this task with your current experience in this unit, reflect upon what you have read about blogs.
In your learning log, record your thoughts. Consider various uses for blogs such as citizen journalism and personal blogging. Have you seen in your net travels any interesting uses for blogs? This blog entry is an opportunity to tell us what you really think of blogging!
The attention economy is what blogging has succesfully developed over time, it has not only allowed many areas of the community to get in touch and develop the infosphere but also allows people to communicate into the infosphere by inputting there knowledge online to allow them to share there own insight on the web.
Todays info technology world we saw the cam recorder develop from it’s early stages and now plays a important part in web pages via webcam and we can also remember how it developed and started in the world of recording news stories and current and various issues, we then saw how this could be added into your website to develop it a fraction further by giving windows media examples.
Really see blogging as a development of the web matrix, blogging as a element allows the user to give your own personal views and development out on the web than just live in social isolation, it does have it’s positives but also has it’s negatives that someone still can gain a detailed profile of you and aspects of your life, so the element of security still has to be in you.
Blogging is a great development of the web as it gives you the most intimate interaction with web users, but you clearly have to take on board the most appropriate rules of web development that include the top 5 conventions of web pages by Dennis G. Jerz. You really have to take into consideration that there are many aspects of blogging and to entertain a audience with clear concise information is vastly better and more intelligent than just creating a blog out of thin air.
Blogs are a project that need to be heavily reasearched into if you with to take it to such standards of citizen journalism, if it’s a simple blog about you please just consider the elements of Dennis.G.Jerz report as it will allow you to develop a professional standard threw your blog.
Many blogs I visit have to do with my interest level on many different subjects, may it be North American Union to how video games affect people, and if I need a world wide view on all gaming I would go to other countries to plod threw the data that is presented.
But overall at the start of this project I listed some valueable points for bloggers and I can still see that the same points are really indication on what we need to do as a factor of creation of web blogs ensure that you stick by all methods and research to ensure that your blog is unstandable.
Web 2.0
Now you’ve read about Web 2.0 what applications or “services” do you think are web 2.0 indicative?
Web 2.0 sites that are indicative.
Doing a search on google for web 2.0 and stumbled across a variety of responses including this website that seem to show you alot of growing web 2.0 sites that are already set up http://www.go2web20.net/ .
Deeper understanding about web 2.0, I looked further into descriptions and came across great deal of information with regards to the development of web 2.0 but it’s actually what we already have come across.
Many types of use for web 2.0 come in many forms of blogs,wiki,multi-media sharing services, content syndication, podcasting and tagging services. (1)
Great document promoting active use and implications of that use in education.
http://www.scribd.com/doc/300024/What-is-web-20-Ideas-technologies-and-implications-Paul-Anderson (1)
TASK:
Take a look at the Internet Communications Blinklist we have set up for you as a bookmark site – compared to a html version think about the format and usability of a website/html written list with this same information.
LOG ENTRY:
Whats the difference between the two? What are the benefits? Which format do you think you would like better and why?
There is a difference between the two sites is that Internet Communications Blinklist is clearly defined and logically set out and more appealing than the second site that is basically boring set out. Noticing that one site was Web 2.0 showed it had more capabilities and also gave more in depth options to the site and allowed the site to be set up in a more logical defined manner.
Advancements have now been achieved with Web 2.0 than what was capable with html, these advancements have given clear cut capabilites to include various aspects that extend the power of your web project or production.
Html does not offer as many advanced features that web 2.0 now offers, html is old technology but still is a part of todays web project world. The variable diffence is that one offers more advanced features than the other and that the future is now being placed on web 2.0 protocol and closely developing into web 3.0 in not to distant future.
Learning about the advantages of blogging and now reading about web 2.0 protocols, you can now conclude that their are far more appropriate measures and uses of the capabilites of the web by using this technology and by doing so gain some of it’s best advantages.
References
(1) Anderson, P. (2007). What is Web 2.0? Ideas technologies and implications for education. Retrieved July 6, 2008, from http://www.jisc.ac.uk/media/documents/techwatch/tsw0701b.pdf
Module 2 Chat Task
IMVU CHAT
Every day when I have a chance I participate in Skype chat room, talking to many different people that are involved with Curtin Open Learning Studies. With being involved in a group I asked one night if I could meet two users within the IMVU Chat program and I was totally amazed with the results of this.
I created the name Bartias Cromwell, and joined Kylie from Skype in the IMVU Chat arena, she did have a few system problems as well as I think it was Janet who also had some issues.
Once joining the site and creating Bartias as my character I was bombarded with email messages in my box from automated response robots, that seemed to have a idea that I was playing in there virtual world.
Meeting Kylie inside the main area we did not do much, then another person arrived, I walked into another room which was a constructed nightclub, which was rather interesting. To me it was only of a interest to see what it did.
The graphical componant lacked any super-physics, which resulted in a state of boredom not being able to walk or move around like a character in a game which was a big no no if you want to get people interested in the chat room areas. Now I have found out they they actually have a paid structure of using the system, it is not a game just a means of people communicating towards each other, you can create your own rooms and so and enjoy what you do. OK easy for some, but myself I would rather something more simplified and user friendly that allowed you to move and groove with the groovey chicks like Kylie and Fiona.
I guess beauty is in the eyes of the beholder, but this program was not very impressive at all and the graphic content was just not my cup of coffee.
There were a couple of bonuses in the command structure of the environment that allowed netiquette to be the main priority if people got to abusive or abused the structured system and that was a reporting facilitiy in your command bar, which allows you to have a peace of mind but it still leads you open if you place a false allegation, so how would you respond to that.
There is a creativity side towards the chat, it allows you to create your own rooms that many people can come into and chat in http://www.imvu.com/rooms/ or even http://www.imvu.com/shop/product.php?products_id=1983722&quickfind=new.
In this aspect it goes past the form of a msn type of chat and develops a inner personal space towards the user and the environment for which he has entered, at one stage I was holding multiple conversation with Kylie and someone else inside IMVU main lounge, then suddenly Kylie logged off.
Summarizing the experience, I can see that it would appeal to many people in being able to enter into a virtual world where the worries of the world are gone and you can talk and mix with people in a virtual environment. It has many different aspects that could appeal to people, yet it does not appeal to me cause I guess I am a critical type of person that does not gasp this time of environment because other than gaming in a created virtual world, I would not want to mix with people in it because the factor it’s a hullicination it forms and creates a virtual world in front of you that technically only exists inside the computer.
MSN CHAT
To achieve this task, I had only one person that said they would be interested in doing the task.
MSN messenger has been a part of my web life since the first days I came online, I find MSN very key part in communicating it is straight down the line very good chatting software, with little emphasis on online adverts.
What has turned me off ICQ is the fact of security and that Microsoft constantly keep their updates up to date and there is less amount of issue with regards to spam bots, it creates a viable internet world for you to respond to those who you wish to talk to.
Msn Messenger provides functions to deal with those people who do not have good netiquette, you have the ability to block these people and report them as spammers which is a good and very handy tool.
Within communicating with Andaleepb, the communication was coming across very easily except for the constant fade in and fade out which could have been that she was on a ADSL connection and that my connection was Cable, fading voice chat could link back to connection use or even possibly be the systems setup.
Key aspects of MSN messenger is its structure that it not only allows you to send and receive messages over one media but then in branch’s out into the world of mobility and gives you capabilities of staying in touch with other people.
The many aspects of the MSN Chat are below please click on a box to see the contents:-
You can click on each individual file and obtain the command structure of the program it gives you a glimpse of the possibilites and capabilities you have at your finger tips. Another very good aspect of MSN messsenger is the capability of storing previous conversations with people so you can recall your last conversation. Their is no hidden costs involved and their is no gastly over-imbudance of spam bot mail or adware like IMVU.
Really this is a quite personal way to talk to others in a care free environment with no impending issues developing over time that could cause issue, microsoft constantly update there security patch’s so there is no worries there. In this environment you are what you make it and others see you on line they can chat with you and you can chat with them in a vice-versa environment, there is no hullcingene created environment to keep the eyes stimulated.
You have the option of text chat and also voice chat, and also the superior option of staying in touch via SMS mobility which is quite handy to those who can afford the price over time.
Summary I think MSN offers alot better qualities than ICQ, I have had a lot lesser issues develop with regards to viruses and bugs and also quirks by sticking to what is offerred by Microsoft. The product achieves the exact same result being able to talk to the other person in a internet created environment instead of the old telephone call, which enables the person to complete there every day tasks instead of being interuppted at the telephone conversation. In todays environment messenger software really has it’s bonuses in capatilizing on saving money via staying in touch with your friends while being able to manage your time vastly more than ever before.
One must remember that with every type of advancement you always need to keep your security and privacy under control by occasionally reading and keeping software updates running in order to protect your system from flaws that could be used by other malicious users that are on the web.
Email Tasks continued
Email Lists
Think about the following questions (it may help to discuss them with other students on the discussion board)
- What are the pros and cons of email lists versus discussion boards?
- Are there certain kinds of communication or purposes more suited to one than the other?
Email Lists
For this I decided to join the group task that was set out by Cynthia.
http://au.groups.yahoo.com/group/internetstudies
My name on this email list was dux1491; I carefully looked at what was on offer and joined a few other types of lists that were available to see the differences.
Lists – Pros
A) Email is sent to directly to your account, keeping you informed.
B) Allows creativity as every users input will be vital to the list.
C) Some lists set a guideline of what they would like to know about you, they send this as a part of there moderation teams effort to keep in touch with you.
E) Topics flow more which sets a interesting discussion to take place were people’s opinon count more, because they have the freedom of speech.
While there was no generalized set of rules for internet studies sent to me I was clearly notified after joining the other group located on the same site. Church of Christ sent me a valid list of Church of Christ@yahoogroups.com.
MODERATORS’ POLICY STATEMENT ON PERSONALITIES, DIVISIVE ARGUMENTS, AND LIST DISCIPLINE (September 28, 2000)
This kind of developed list that gives the list team members be given the rules and told what is acceptable public debate and talk, and what is not acceptable.
Lists- Cons
A) With the amount of mail that I was receiving by just joining the list, you would defiantly need an established rule structure for your mail box. I bypassed this problem by creating a yahoo account so my email inbox would not be as affected so much.
B) More time needed if something goes wrong with regards to what you are saying on the list particularly on the yahoo email list.
C) You have to find the archives on a web site, so they are less accessible than on a discussion board. With setting this up I had to join yahoo in order to access the full list of what was offered in there email list.
D) Knowledge is very limited to only who is on the list so it dampens the view to a very short view point than many other mediums.
Newsgroups
Newsgroups-Pro
A) Forte Agent is a great program and found that the search functions in it very useful, many different other programs out there contain similar email functions, so a combination could be good.
B) Newsgroups can bring people together to share a common interest.
C) Newsgroups allow you to understanding vast amount of topics in a variety of areas, similar to email lists, but on a wider audience.
Newsgroups-Cons
A) Obtaining illegal material is easy via Usenet posts, very dangerous for younger viewers.
B) Flaming and constant abuse is a popular aspect of Usenet
C) Pedophiles and other underground types of people lurk within Usenet greater than normal web.
Path: news.optusnet.com.au!newsfeeder.syd.optusnet.com.au!news.optusnet.com.au!not-for-mail
From: Chris <ardist@hotmail.com>
Newsgroups: aus.sport.cricket
Subject: Michael Beaven
Date: Tue, 17 Jun 2008 16:40:48 +1000
Message-ID: <eume54pba9doaenlnod5t2o643d0iecvli@4ax.com>
X-Newsreader: Forte Agent 4.2/32.1118 trialware
MIME-Version: 1.0
Content-Type: text/plain; charset=us-ascii
Content-Transfer-Encoding: 7bit
Lines: 10
NNTP-Posting-Host: 220.237.87.168
X-Trace: 1213684840 30463 220.237.87.168
Xref: news.optusnet.com.au aus.sport.cricket:116913
I really miss Michael Beaven, he was a great Australian player, would
have made excellent Captian Material.
http://www.youtube.com/watch?v=Pd2J7GuL-CI
Big Wicket, but who bowled him over to force his hand into retirement from the game?
Michael Beaven RIP.
Are there certain kinds of communication or purposes more suited to one than the other?
Researching and weighing in the pros and cons to both products newsgroups and usenet, email lists could be vastly better option than newsgroups for many purposes that also include security for your children while viewing the web.
Newsgroups have there grey areas that could allow allot of pedophiles that can lurk in this area and I find that would not suit the most people once they work it out and that email lists can be moderated successfully and managed more coherently than just that of Usenet feeds.
Usenet newsgroups are the older version of the two and have been within the net for a vastly long time, but I find the non-filtering of them really destroys the communication process and capabilities of it. Newsgroups would have had a great ability to be used correctly but yet like many applications I really have come to the conclusion yet again only a selected few people would even know about it as the World Wide Web is pushed more via google and so on, it becomes vastly more appealing to join a email list.
Only major issue of email lists is the fact that any new posts will automatically get sent to your inbox therefore it is wise to set up your message rules so that you can especially file and delete the posts that you do not need.
The moderation of email lists provide a more successful and also encouraging method of discussing situations or topics depending on the pro’s and cons and what the product is going to be used for there are things to weigh up, I found newsgroups utterly filled with boring posts about how to become rich over night and pornographic type love letters and filthy language, yet not much moderation.
I then found email lists to be moderated that allowed the subject to be kept on that the subject without straying, it was also interesting to see the rules sent to you to ensure the integrity of there email list be kept upon a new user joining the group.
As the internet grows vastly more people will be introduced to discussion forums on the world wide web, it would take vastly greater amount of learning by the person to understand how the functions of newsgroups work, and therefore I find that email lists could be greater than newsgroups.
After posting my topic about Michael Beaven on newsgroups nobody at all responded to it, it was like talking to a brick wall and receiving not even a comment, vast amount of posts were either knocking others or commenting on previous cricket match’s.
Just remembering the key aspects of net ettique when speaking in the public arena it is a vital component towards enjoying your internet, there is no need to get into serious heated arguements over anything, develop yourself as you develop your online interest.
Module 2 Email Tasks
1. What information about a user’s email, the origin of a message, and the path it took, can you glean from an email message?
Emails contain a lot of different data that can be gleaned from them for example.
Consist of: username@domain.
The username is that for which the person is using on the domain server.
Mail leaves your system the first thing the network looks for is what domain will it be sending to, and then the username directs it to the user that is involved with the sending process.The username@domain is similar to the address in local Australia Post Mail, it has to be on the email or the email will simply either reject and bounce back to you and come up as a mail delivery system error.
The vital component in email is definitely the username without it; your computer will reject sending the mail via alerting you something is wrong. With the wrong user name and only a domain name you could accidentally send email to someone who you never meant to send to who was in your contacts at the same provider.
So in all, the most vital component the user name and then the domain.
By going file properties on the email that you have received you can gain in depth knowledge with regards to the path that the email has taken.
For example this is what a email header looks like all digital information has been altered:-
Return-Path: <billclinton @yahoo.com>
Received: from web32003.mail.mud.yahoo.com (web32003.mail.mud.yahoo.com [68.142.207.100]) by mail18.syd.optusnet.com.au (8.13.1/8.13.1) with SMTP id m5ABNXUq014299 for <johdam@optusnet.com.au>; Tue, 10 Jun 2008 21:23:35 +1000Received: (qmail 66193 invoked by uid 60001); 10 Jun 2008 11:23:31 -0000DomainKey-Signature: a=rsa-sha1; q=dns; c=nofws; s=s1024; d=yahoo.com; h=Received:X-Mailer:Date:From:Reply-To:Subject:To:In-Reply-To:MIME-Version:Content-Type:Message-ID; Received: from [68.186.22.15] by web32003.mail.mud.yahoo.com via HTTP; Tue, 10 Jun 2008 04:23:31 PDTX-Mailer: YahooMailWebService/0.7.199
Date: Tue, 10 Jun 2008 04:23:31 -0700 (PDT)
From: BillClinton<Bill_Clinton@yahoo.com>
Reply-To: Billclinton@yahoo.com
Subject: maxwell
To: JohDam<JohDam@optusnet.com.au>
In-Reply-To: <AA62CF1784FB4BCCBA9E5B5876C71D15@RavenClaws>
MIME-Version: 1.0
Content-Type: multipart/alternative; boundary=”0-1848670995-1213097011=:66101″
Message-ID: 826003.66101.qm@web32003.mail.mud.yahoo.com
A few different sorts of information can be obtained from this email message header.
A) The Usernames BillClinton@yahoo.com and Johdam@optusnet.com.au
B) The Mail Server names :- web32003.mail.mud.yahoo.com and the IP address.
Mail18.syd.optusnet.com.au and IP address
C) Date and time of the email arriving.
2. In what cases would you find it useful to use the ‘cc’, ‘bcc’ and ‘reply all functions of email?
When sending emails there are a variety of tools available to you as a user, but these are the main keypad to your successful sending and receiving of email.
Create Mail allows you to create your mail, ensuring that you have the email address of the sender; you then can create and send emails online.
If you wish resend to the exact same users/group that you have been communicating to reply all will allow you to send to the whole group involved with the email.
This is where email as a tools is a more viable component than just ordinary Australia Post mail, because we not only have the function of being able to send to one person at one time, or then hit reply all and respond to multiple people at once time, emails gives vastly more benefits in saving time than just ordinary mail.
Reply All also works when receiving email from one person who has posted to a list of people, you may then click on reply all in the tool box to achieve a multiple reply towards all on the list and will also include yourself in that reply.
CC: – Is good enough for me to use in majority of my emails. CC is known as carbon copy it allows you to send either a copy onto another machine or another account, or like myself I use it when I email my American friends so that in one key stroke I can stay in touch with them.
Bcc: – A Bcc (blind carbon copy) is a copy of an email message sent to a recipient whose email address does not appear in the message.
Every recipient of the message can see all the To and Cc recipients, but does not know about Bcc recipients.
Remembering, learn how to use these functions correctly the functions be so careful on how you use them or it will result in a personal dilemma for you.
These functions work well in group activities, be sure to use them well as they can often lead to mix ups, I was stupid enough once to hit reply all and tell one person’s group listing how much I hated her images that she sent me of certain stuff, the person was not to impressed.
3. In what ways can you ensure that an attachment you send will be easily opened by the receiver?
A) Most Internet Service Providers in Australia have a limitation on what you can send via email of around 5meg to 10meg depending on how there mail server handles the traffic, Hotmail and Yahoo can receive bigger files.
B) To ensure your receiver can open the attachment correctly, you would first have to ensure they understands how to use that attachment correctly therefore it would have to be in a familiar format depending on.
C) Ensure that the attachment can be easily downloaded and that the users machine can take attachments, as some email settings not set correctly.
D) Ensure that you send the attachment using a generic file format that they are familar, often pdf,rtf can be easily downloaded as attachments.
E) Compression maybe used if the files are larger files in order to shrink the size so you can furfill your isp requirements.
F) Communication with the receiver of your email is a vital and key component in sending, if they have no clue on what they are doing to download the file, you will need to carefully explain to them which will take up some time, sometimes often include in your email what program you need in order to get the file downloaded correctly.
4. What sorts of filters or rules do you have set up, and for what purpose?

At the moment I don’t have any filters or rule set up for my inbox, but when I was in business on eBay I relied on them to. Filters are designed to allow you with the ease of email that your inbox does not get clogged up with to much emails over time. You can specifically set a file structure in your inbox that allows you to store specific emails from friends or businesses or such sites as eBay that you can specifically go to these folders instead of your in box.There are a variety of rules that you can set up, and then the action of the rule be applied to the email address or email list.
5. How have you organized the folder structure of your email and why?
My folder structure is generic, I really have not much use in filing as I keep the folders down to a limited amount so that there is not much to control. I like a KISS approach because really email is simply that email, you read it and delete it.
I do see the viable method of having a controlling structure that is similar to that of a filing cabinet, only if it is viable. To me I get messages from friends I deal with the messages straight away. With my emails there is no need to create a filing structure via rules because the majority of my emails get deleted within 24hrs.
Organizing rules and your folder structure is very important when running a business because you can basically get the computer to do the work for you, just like the old days when secretaries did the paper work, computers have create the virtual office so they can ease the problems for you.
Folder structure is important, but having the right rules that control the data in the folder structure is most important, you don’t want emails to get lost that are very important.
Four Main Personal Aims of Module Net 11
To learn alot of new interesting things about the Internet.
To mix with my peers in the discussion forum areas.
Ensure my grammar is reasonable enough for anyone to read.
Slowly develop my blog into a worthy project.
Bibliography
Module 3
(1) Anderson, P. (2007). What is Web 2.0? Ideas technologies and implications for education. Retrieved July 6, 2008, from http://www.jisc.ac.uk/media/documents/techwatch/tsw0701b.pdf
Module Four
Robert, Pastor Toward A North American Community. Retrieved August 27, 2008, from http://www.american.edu/ia/cnas/pastortnac.html Web site: http://www.american.edu
Pastor, Robert Toward A North American Community. Retrieved August 28, 2008, from http://www.american.edu Web site: http://www.american.edu/ia/cnas/pdfs/Pastor_Worldnet.pdf
Blanchard, Kate (October 31, 2007 ). Revisiting NAFTA. Retrieved August 28, 2008, from http://apps.carleton.edu/campus/sustainability/Shrinkingfootprints/ Web site: http://apps.carleton.edu/campus/sustainability/Shrinkingfootprints/?story_id=346841
Module 5
Nardi as a ecological system, Curriculum Module 5 retrieved August 27 2008, (Nardi & O’Day, 1999)
Allen M (n.d) Net 11 Curricullum Module 5. Retrieved August 27th 2008.
Lerner, M (1996-2008). Learn the Net: The future of the Internet. Retrieved August 27, 2008, from Learn the Net:Future of the Internet Web site: http://www.learnthenet.com/english/html/03future.htm
‘Net Neutrality’
http://www.google.com/help/netneutrality.html
Pollick , Michael (2003 – 2008 ). http://www.wisegeek.com/what-is-net-neutrality.htm. Retrieved August 28, 2008, from http://www.wisegeek.com/ Web site: http://www.wisegeek.com/what-is-net-neutrality.htm
-
Recent
-
Links